
Most Docker container security best practices at the time of its initial release involved checking Docker container images for flaws. A far more thorough approach to security is now considered best practice due to the widespread usage of containers and the development of container orchestration systems.
We’ll go through the security measures you can take to ensure your Docker environment, host, and containers are operating as safely as they possibly can. Knowing the appropriate container security solutions is crucial, given the growing use of Docker and containerization.
What is a Container?
An operating system virtualization technique called containers lets you execute a program and its dependencies in separate processes with their own resources. These different processes can operate independently on a single server without being able to see each other’s data, networks, or processes. Each container instance typically offers just one service or discrete functionality (a microservice), making up one part of the program.
Since containers are immutable by nature, any modifications to a running container instance must first be made to the container image before being deployed. With this functionality, containerized apps can be deployed with more assurance, and development may be expedited.
Container Vulnerabilities
The Host Operating System’s Security
Infrastructure layer security is where container and docker image security begins and is only as robust as this layer. Attackers may affect all OS processes, including the container runtime, if they take control of the host operating system (OS). Therefore, the base OS should be configured to solely operate the container engine, with no other processes that could be vulnerable, for the most secure architecture.
A Linux distribution is the host operating system of choice for most container users. A best practice is often to use a host system designed specifically for containers to lessen the attack surface. For example, red Hat Enterprise Linux CoreOS, which is hardened with SELinux and provides process, network, and storage isolation, powers contemporary container platforms like Red Hat OpenShift. You should always maintain the host operating system patched and updated to further fortify the infrastructure layer of your container stack and enhance your overall security posture.
Securing Docker Images
Static examination of your container images using the built-in techniques reveals any potentially weak OS and non-OS packages. With policy checks inside a secure container development process, you can decide if you want to promote non-compliant images into trusted registries using an automated tool.
Enforcing policies is crucial because susceptible pictures that enter production systems offer serious risks that can be expensive to fix and harm your organization’s reputation. Consider the security of the programs that will execute within these images.
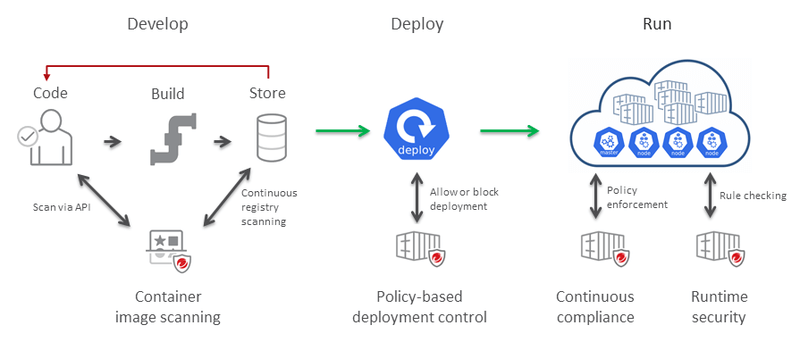
Securing Docker Runtime
Your whole container security approach must include Docker runtime security. It’s crucial to set up monitoring software for the active containers. The alerting systems must be in place to halt and replace the vulnerable container as soon as new vulnerabilities are reported that affect a specific container.
Securing the registries where the pictures are stored is the first step in protecting the container runtime. The ideal approach is to only download and execute images from reliable container registries. You should only promote trustworthy and signed pictures into production registries to offer an extra degree of protection. Images that are readied for production deployments shouldn’t exist in container registries with vulnerable, non-compliant images.
Best Practices for Container Security
Docker Image Scanning
You should examine the packages and components contained in the image for widespread and well-known vulnerabilities as part of a continuing effort of docker image security. Image scanning needs to be able to find weaknesses not only in the base layer but also in the other levels as well.
Using a Trusted Base Image
Ensure the container image is based on a different well-known and reliable base image that was obtained using a secure connection. The Docker community or a connected vendor curates and optimizes Docker images in official repositories. A developer’s practice should be connecting to and downloading pictures from safe, reputable, private registries. To minimize attack surfaces, these reliable pictures should be used wherever feasible from minimalistic technology.
OS Updates and Vulnerabilities
It’s crucial to establish best practices and software to confirm the versioning of the underlying OS’s packages and components after choosing an operating system. Be mindful that if you choose to use a container-specific System, it will have components that could wear out and require maintenance. Using the tools provided by the OS vendor or other trustworthy firms, you should routinely scan and check for component upgrades.
Choosing the Right OS
You must control each security element separately while using a general-purpose OS. Container hosts shouldn’t run any extraneous system services or non-containerized programs. You should also routinely check for vulnerabilities in your host operating system. Apply fixes and system updates if you discover vulnerabilities.
Access Management
Every direct OS authentication should be tracked and recorded. Only the proper users should be given access, and keys should be used for remote logins. Also, you should set up firewalls and restrict access to only reliable networks. Also, you want to put in place a strong log monitoring and management procedure that terminates in a specific log storage host with limited access.
No Secret in Dockerfile
Keep your secrets out of container photos. Developers could occasionally hide AWS keys, API keys, and other secrets inside photos. These keys might be used against the assailants if they were to steal them. Secrets should always be kept separate from pictures and made available dynamically as needed during runtime.
Summary
It is true that environments and apps that use containers raise extra security issues that do not apply to non-containerized applications. Yet, you may establish a stronger security posture for your cloud-native environment by adhering to the basic core ideas for host and application security described below.
Additional security best practices like scanning application source code (both open source and proprietary) for vulnerabilities and coding errors as well as adhering to a policy-based compliance approach can significantly improve your container security. Host security, container image scanning, and runtime monitoring are excellent places to begin.
Related: Benefits and Drawbacks of Docker
