Kubernetes is currently the most used container orchestration platform in the world. Many businesses have begun deploying microservers and CI/CD configurations with the assistance of Kubernetes. The default configurations of Kubernetes could be vulnerable in several different ways. Given that the organization is the one managing Kubernetes, it follows that the company is also responsible for ensuring its safety.
It is essential for every organization to put in place security and compliance procedures to ensure that their daily business activities are carried out without a problem, to safeguard their reputations, and to determine the right level of risk for each application. For the most part, compliance frameworks are used to answer security and privacy concerns through the simple monitoring of controls, the assignment of accountability at the team level, and the assessment of vulnerabilities.
All of these things present unique challenges in an environment that uses K8s. Therefore, it is vital to deploy or use tools that can flag security and compliance issues, enabling organizations to take the necessary steps to protect themselves.
Open Source Compliance Tools for Kubernetes Application
One of the greatest priorities is managing the appropriate level of security and compliance. This is particularly important because a significant number of microservices are currently being deployed using Kubernetes or containerized applications. However, manually doing these processes can be very time-consuming; as a result, organizations typically use open source tools that check security and compliance inside the deployed infrastructure itself. Let’s discuss a couple of open source tools we can use to ensure proper posture of our K8s.
Kubescape
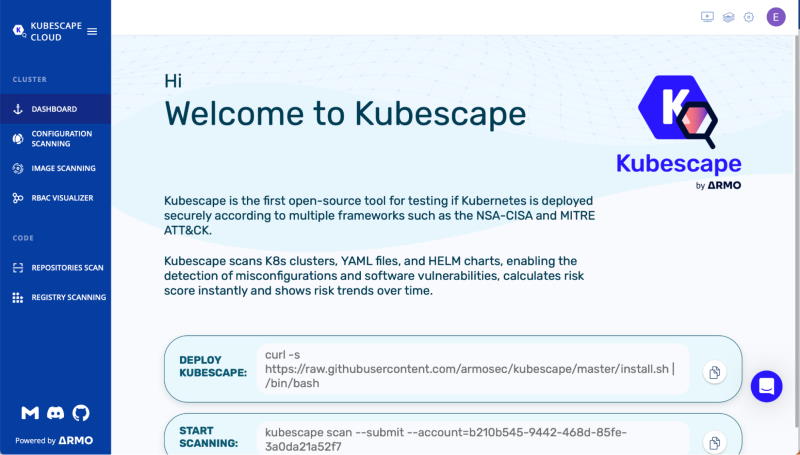
Kubescape Cloud is a cloud application for Kubernetes that has a number of features, such as risk analysis, auditing for security and compliance, and even RBAC visualisations. It also has a feature called “image vulnerability scanning,” which makes it easy to look for issues or security flaws in image components. Kubescape looks at K8s clusters, YAML files, and HELM charts, among other ways to deploy, to find wrong configurations.
KubeScape Cloud runs on KubeScape, which is a free, open-source tool that can be found on Github. You can send data to the Kubescape Cloud using the Kubescape, which will give you a better outcome from RBAC and image scanning. For example, you can use different filters in RBAC to see which users have which roles. You can use the configuration scanner to find problems with the configuration, like if privilege escalations are allowed, if audit logs are turned on, etc. Kubescape Cloud’s ability to scan not only saves time and money, but allows early-stage bug fixes.
TerraScan
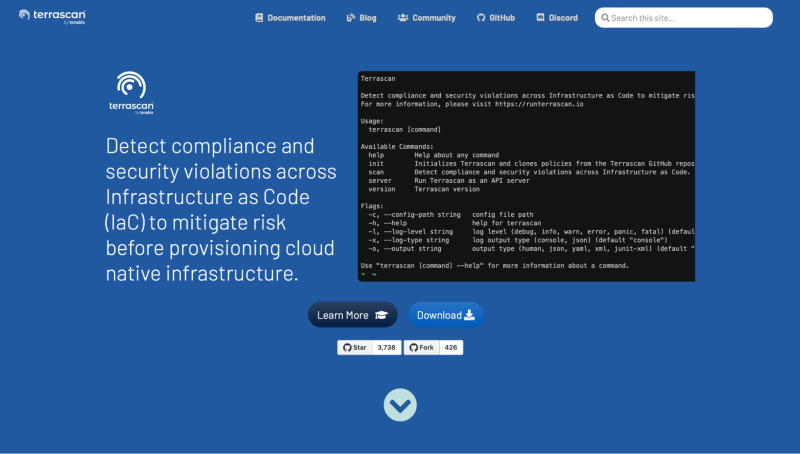
TerraScan is a static code analyzer created by Tenable. It is used to analyze the codes deployed inside the infrastructure. It performs a complete and seamless scan of the infrastructure as code to locate any misconfigurations that may exist inside it. In addition to this, it is able to monitor the cloud infrastructure that has been provisioned and detect any configuration changes that can cause problems with security and compliance or damage the security posture of the infrastructure that has been implemented.
It is simple to integrate with CI/CD systems or run locally on its own. Because it is integrated with CI/CD, the organization is able to detect potential security and compliance violations at an earlier stage. It can scan a wide variety of files, including HELM charts, Kubernetes files, and files written in YAML and JSON. Additionally, it has more than 500 different policies for security best practices.
KubeLinter
KubeLinter is another tool for scanning the infrastructure of Kubernetes. KubeLinter analyzes Kubernetes YAML files and Helm charts to locate any misconfigurations that can result in a flaw that compromises the security of the entire infrastructure. KubeLinter executes a number of default checks, the results of which provide valuable information regarding Kubernetes YAML files and Helm charts. Thus, DevOps teams can discover security misconfiguration concerns at an earlier stage with the assistance of KubeLinter.
For example, it can determine whether or not containers are operating in privileged mode. It can also provide best practices that the DevOps team must follow, such as enforcing RBAC. As a result of KubeLinter’s high degree of compatibility, you can enable or disable the checks carried out by the tool and even develop your own tests as per the requirements of your company.
KubeBench
KubeBench is a fantastic tool that discovers any misconfiguration issues that may exist inside your Kubernetes infrastructure. KubeBench conforms to the CIS Kubernetes Benchmark for running tests within the infrastructure. You can execute KubeBench within a container itself, thanks to which you can immediately see if there are any misconfigurations in your deployed infrastructure.
KubeBench has many robust features. It can perform checks regarding correct authentication and authorization, whether your data is being secured while in transit and while at rest, whether RBAC has been properly deployed within the infrastructure, and whether the admission controller has been enabled properly. It basically has a YAML file containing all of the checks. Consequently, if you want to increase the number of checks or specify additional parameters based on the organization’s needs, you can easily do that.
Conclusion
When it comes to Kubernetes security auditing, there are various tools available. Because most of the scanning tools mentioned here are open source, it is easy to check whether they have any bugs or security risks before installing them within your infrastructure.
These tools conduct compliance verification and carry out a great many other checks, such as those for admission controllers, RBAC, picture scanning, and a great deal more. Thus, we recommend first understanding the requirements of your organization and then selecting a product that is compatible with it.
Related: Kubernetes PVC: What is it, and How Does It Work?
Cover Photo by Growtika Developer Marketing Agency on Unsplash
